This blog post shows how to grant access to an AWS account for some external party. For simplicity we will call this external party a "contractor". If you want to do the same for Microsoft Azure look at this blog post instead.
This method requires the contractor to have its own AWS account, but it has several benefits:
- No need to create AWS user accounts for every single person working for the contractor
- You can force the contractor's personnel to use two-factor authentication (2FA)
- You can force the contractor to use an additional password (shared secret)
- You can disable contractor's access completely by just removing the IAM role
This approach works equally well for AWS Console access, AWS CLI and tools like Terraform. Some tools may not like the extra security measures required here or be able to assume a role out of the box.
In the example below we show how to grant read-only permissions to whole of AWS, which is useful for things like auditing, documentation and modeling infrastructure. But what the contractor can do depends entirely on what permissions you grant to the IAM role you create.
Adding a role to AWS
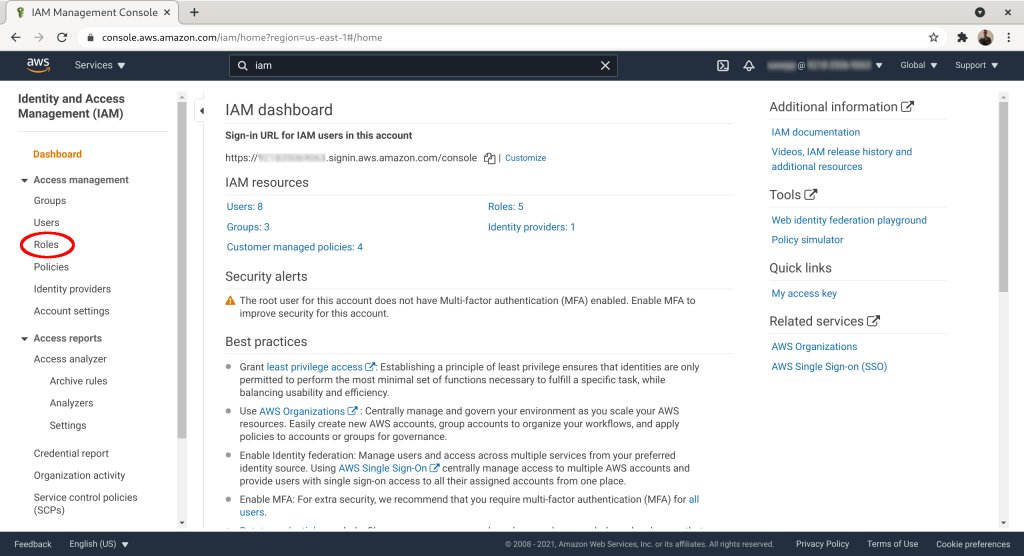
The first step is to add a role with ReadOnlyAccess to your AWS account. The role can then be assumed by the contractor. To do this login to AWS console:
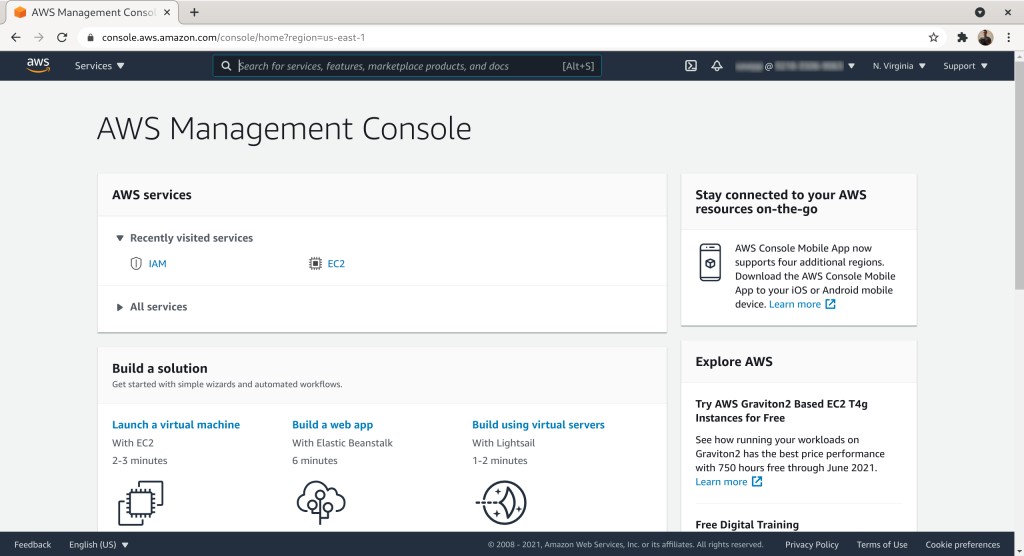
Search for “iam” and then select the IAM service from the list:
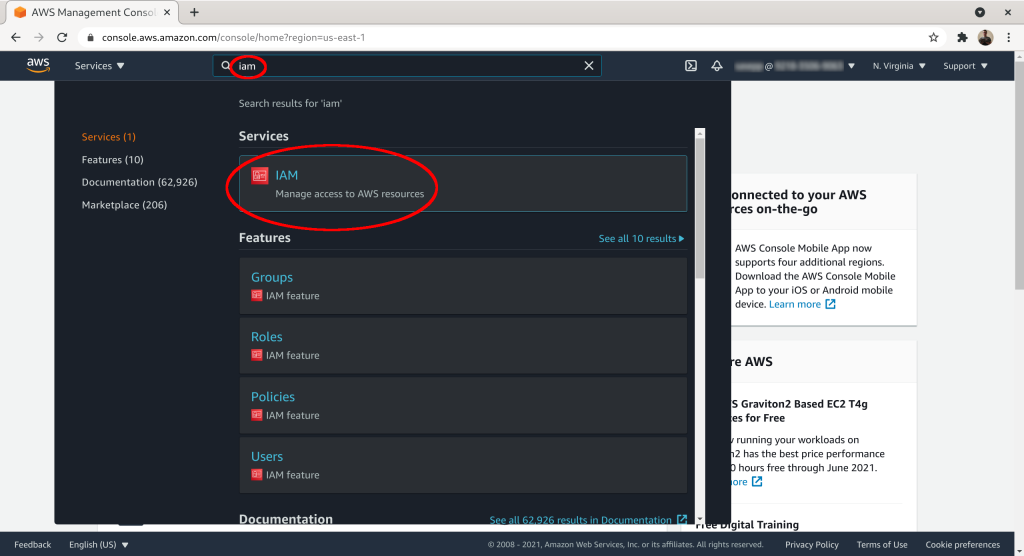
Click on “Access management” → “Roles”:
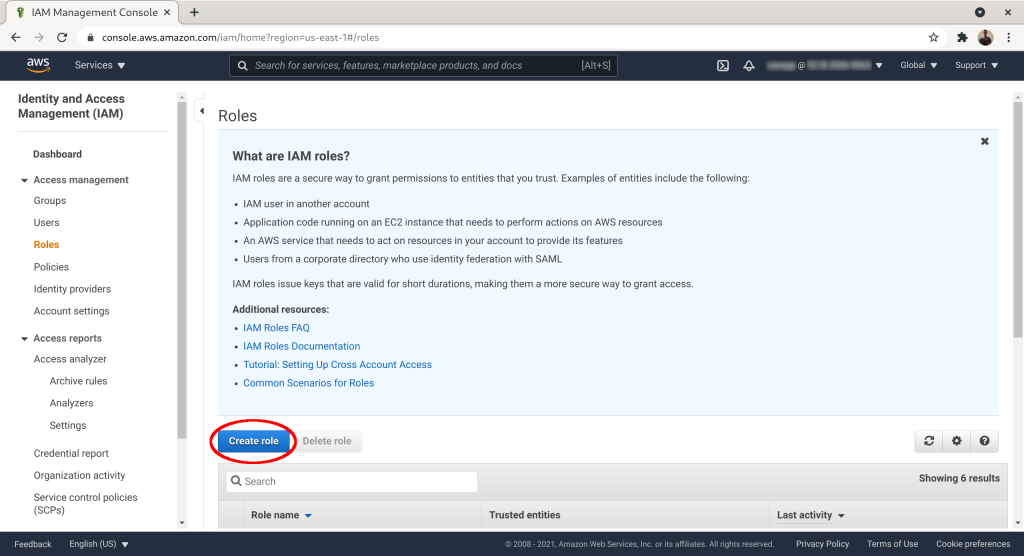
Click “Create role”:
Select “Another AWS Account” as the trusted entity:
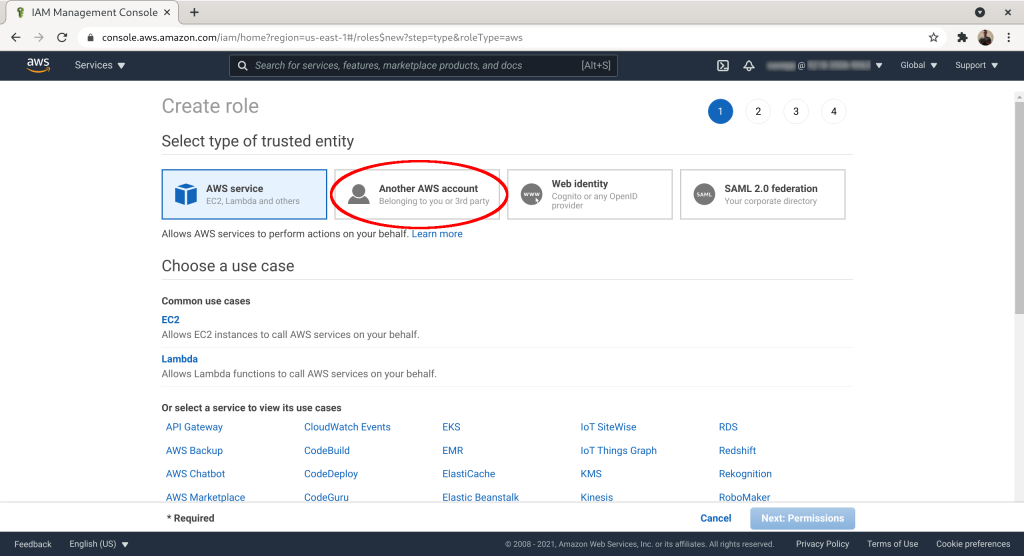
Set “Account ID” to match the contractor's AWS account ID. Add an “External ID” (~password) and check “Require MFA”. Click “Next: Permissions”:
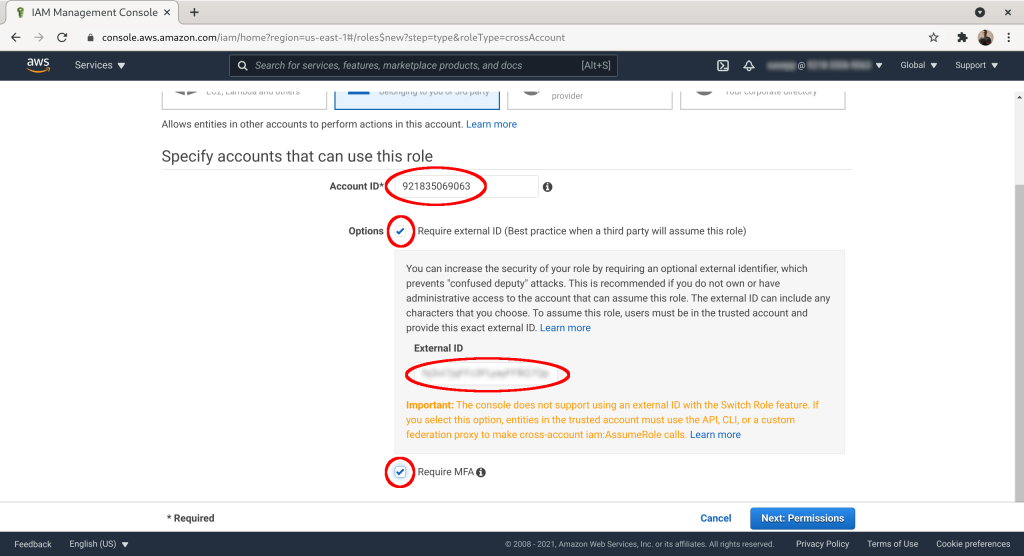
Check the “ReadOnlyAccess” or some other suitable policy from your IAM policy list. Click “Next: Tags”:
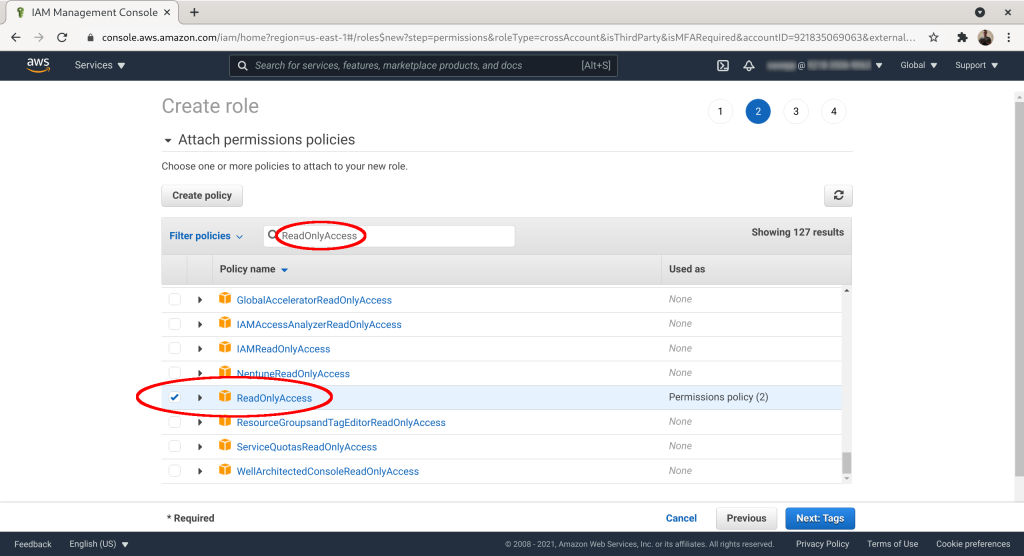
Optional: add tags to the role. Click “Next: Review”:
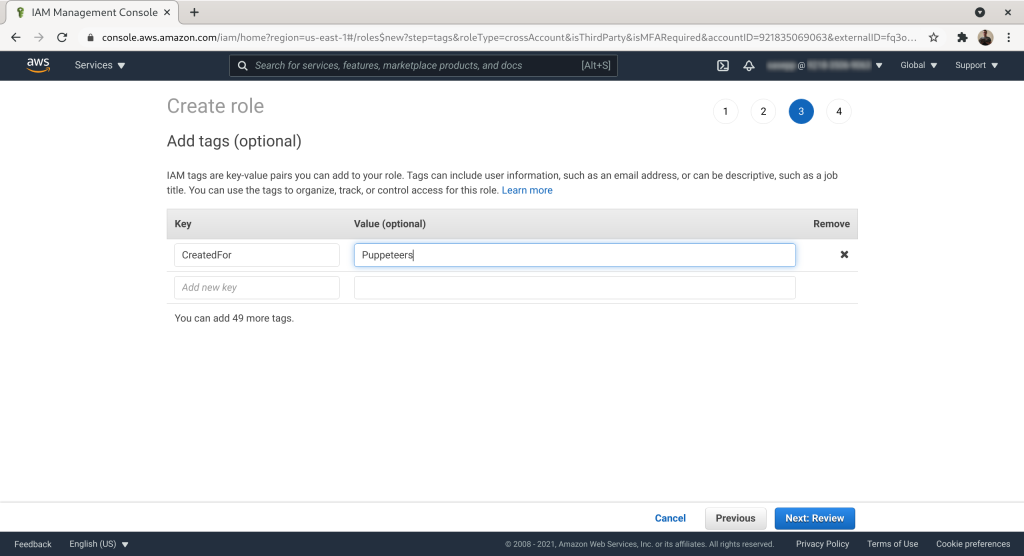
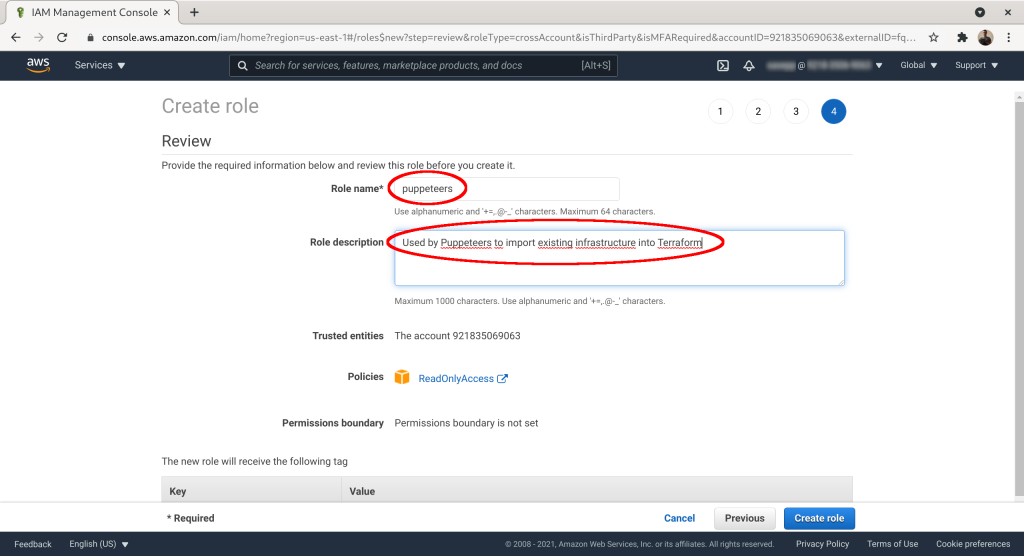
Give the role a name. Here we optimistically use our name “puppeteers”. Add description if you want. Click “Create role”:
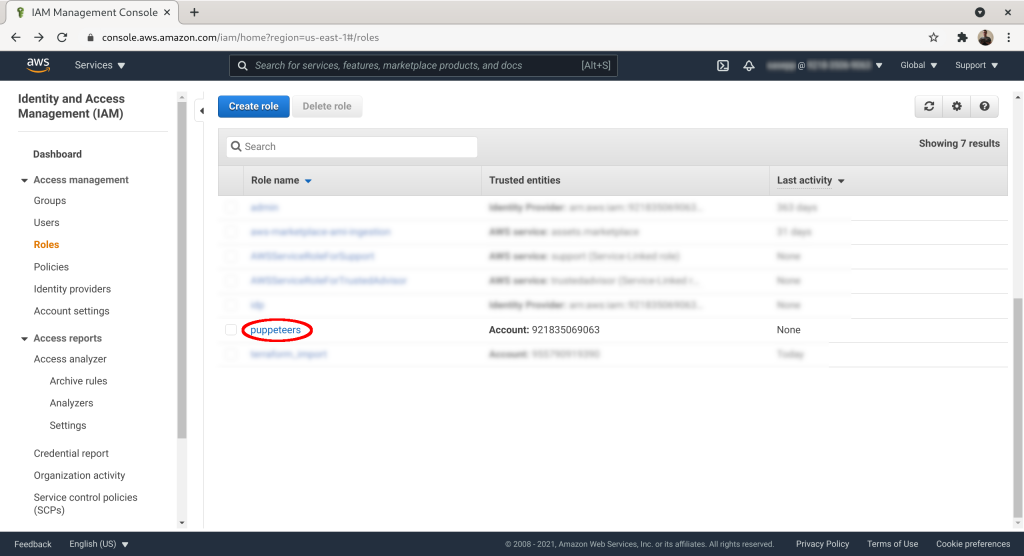
On the role list click on the role you created (here: “puppeteers”):
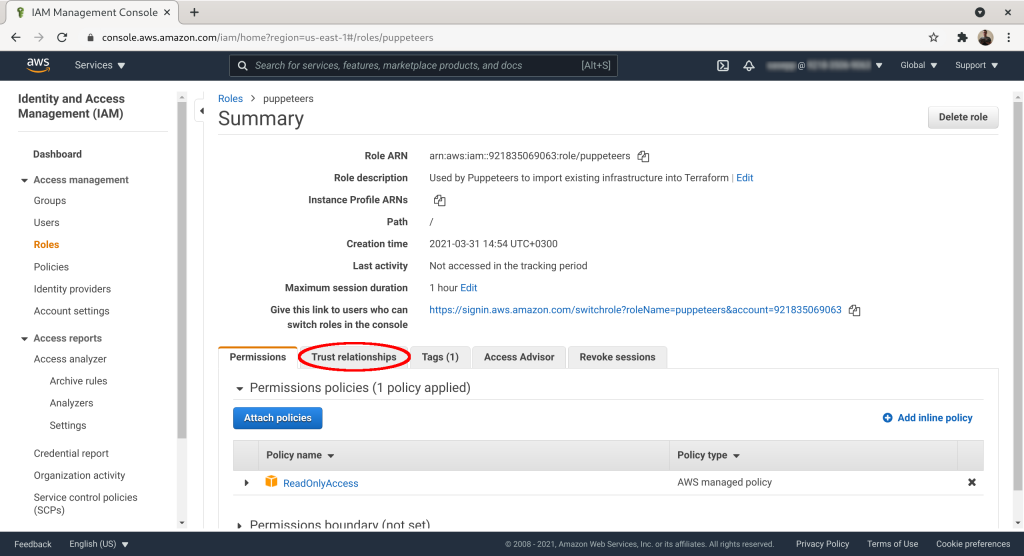
Click on the “Trust relationships” tab:
Mark down “Role ARN” and “sts:ExternalId”:
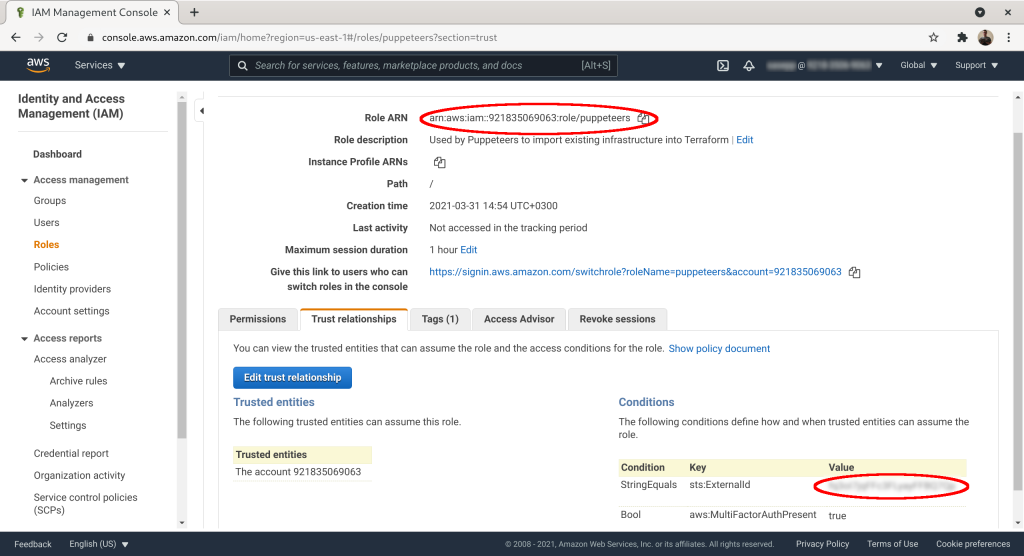
The last and final step is to send std:ExternalID and RoleARN to the contractor. Then the contractor's employees can assume the role you created for them, provided they have two-factor authentication turned on in their AWS account.



