This article shows how to grant read-only permissions for Puppeteers AWS account (921835069063) to your AWS account. This is necessary to, for example, model your infrastructure with Terraform.
Adding a role to AWS
The first step is to add a role with ReadOnlyAccess to your AWS account. The role can then be assumed by the Puppeteers. To do this login to AWS console:
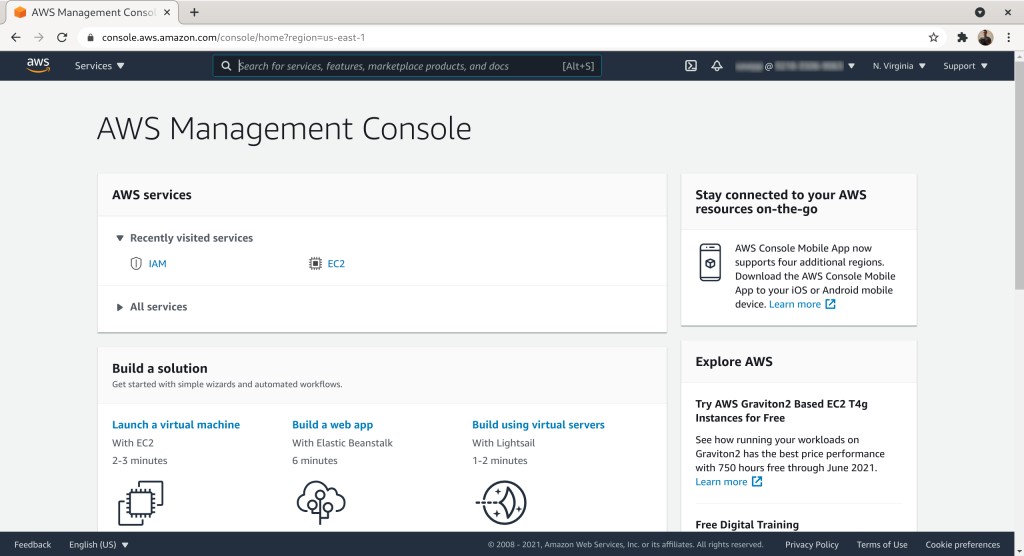
Search for “iam” and then select the IAM service from the list:
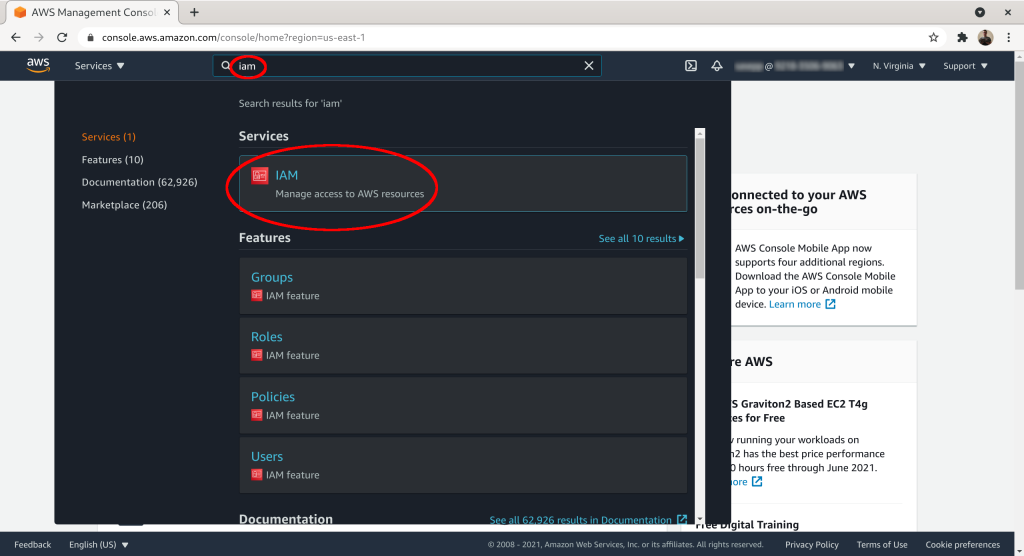
Click on “Access management” → “Roles”:
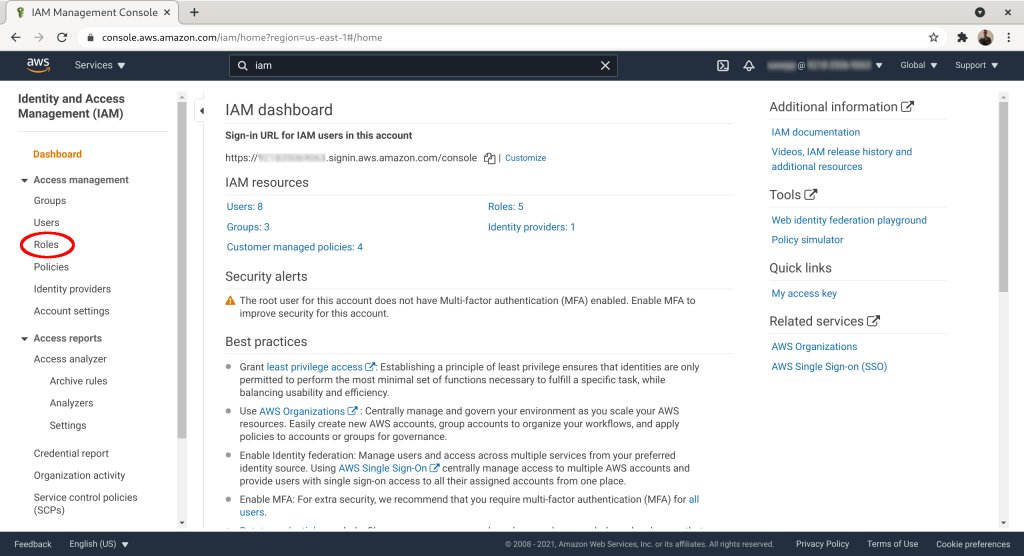
Click “Create role”:
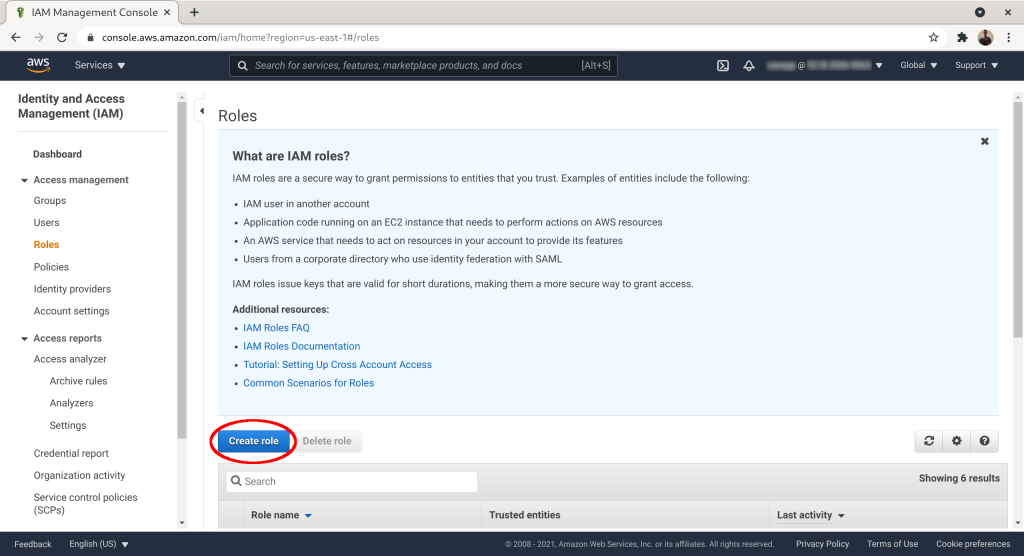
Select “Another AWS Account” as the trusted entity:
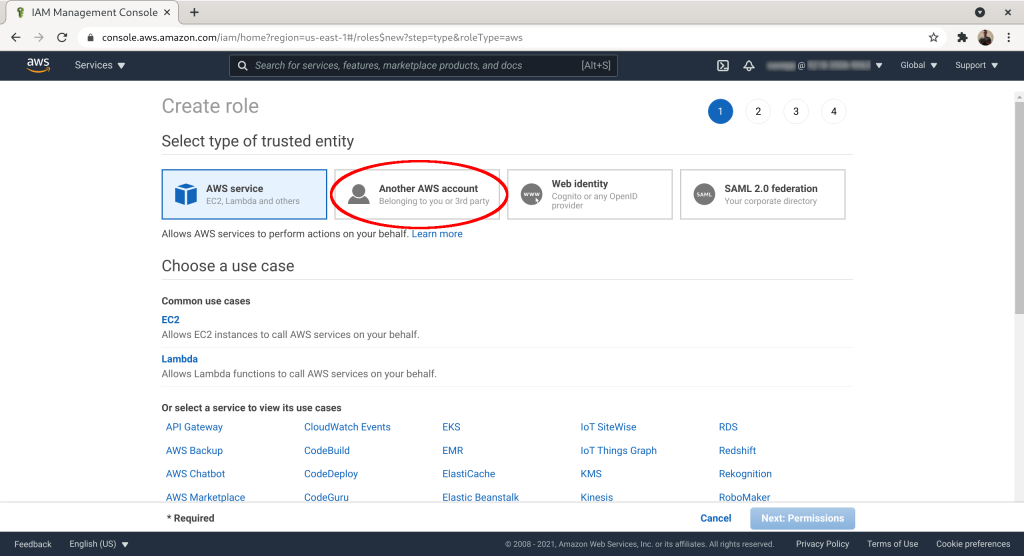
Set “Account ID” to 921835069063. Add an “External ID” (~password) and check “Require MFA”. Click “Next: Permissions”:
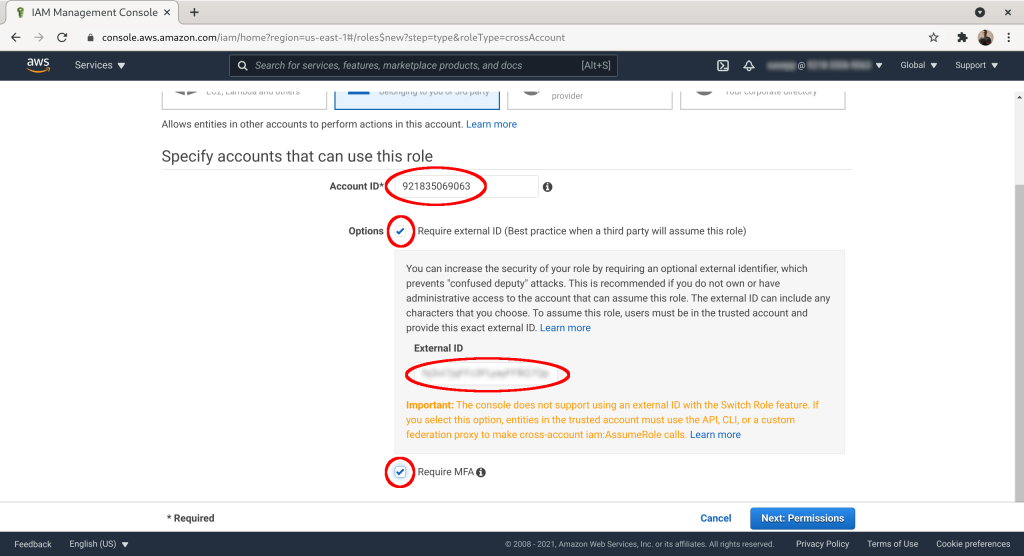
Check the “ReadOnlyAccess” or some other suitable policy from your IAM policy list. Click “Next: Tags”:
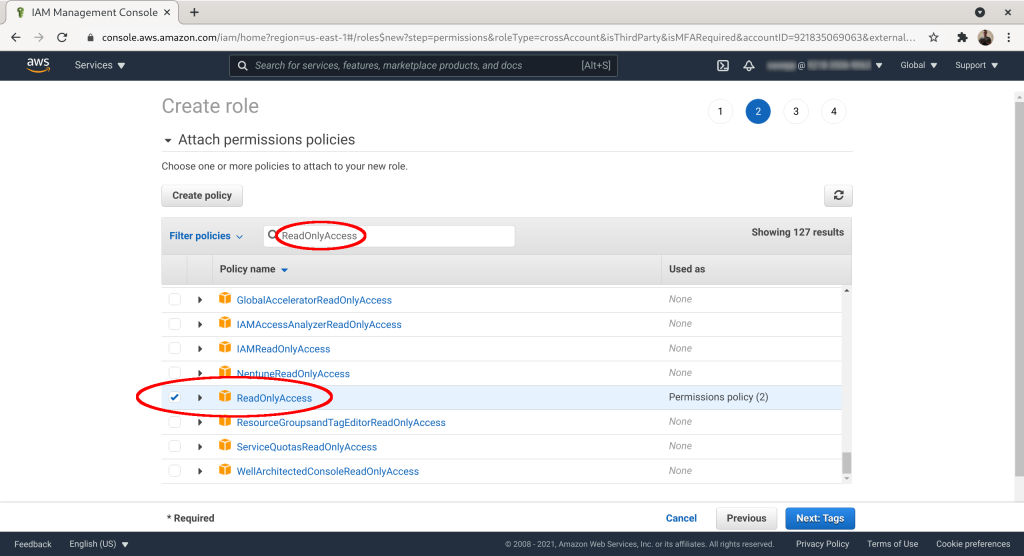
Optional: add tags to the role. Click “Next: Review”:
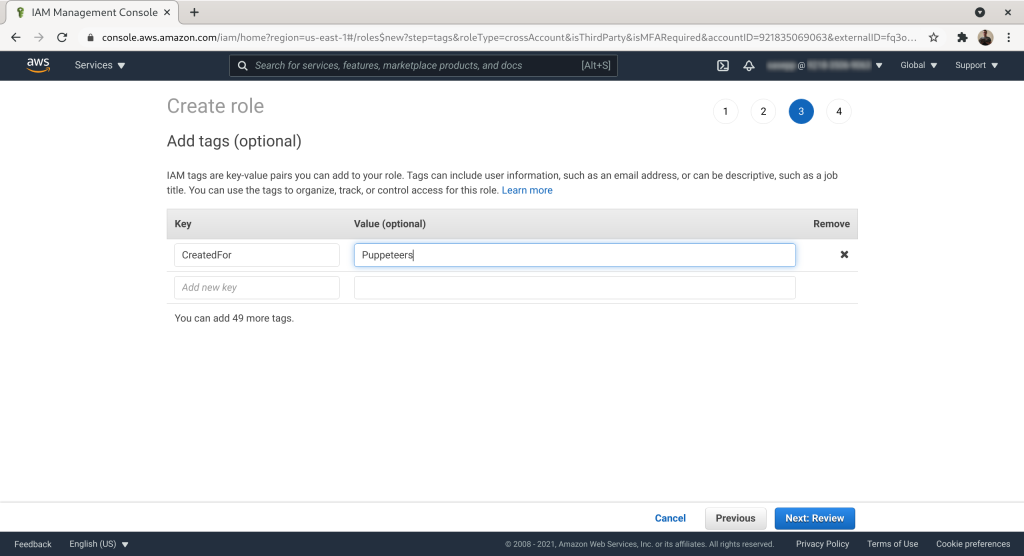
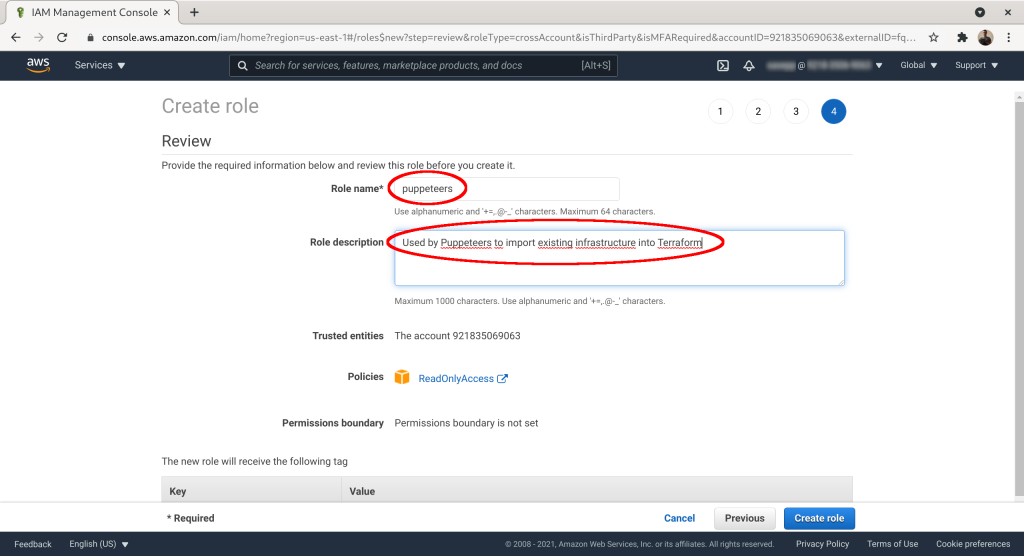
Give the role a name. Here we've used “puppeteers”. Add description if you want. Click “Create role”:
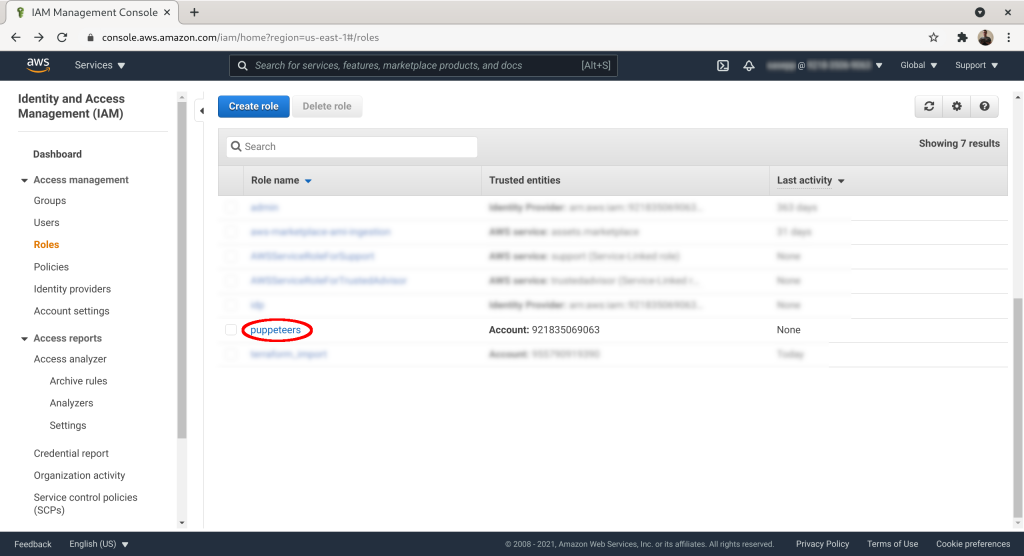
On the role list click on the role you created:
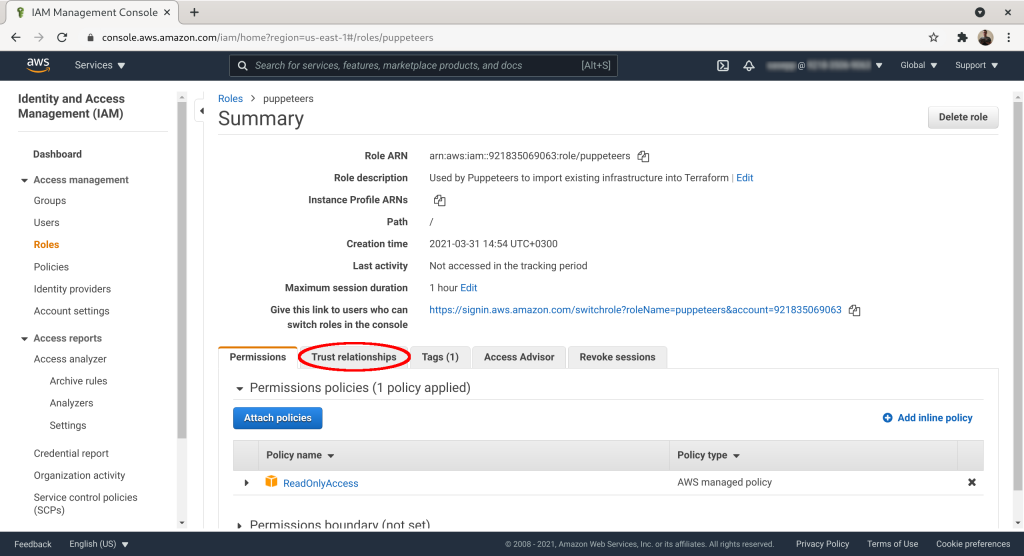
Click on the “Trust relationships” tab:
Mark down “Role ARN” and “sts:ExternalId”:
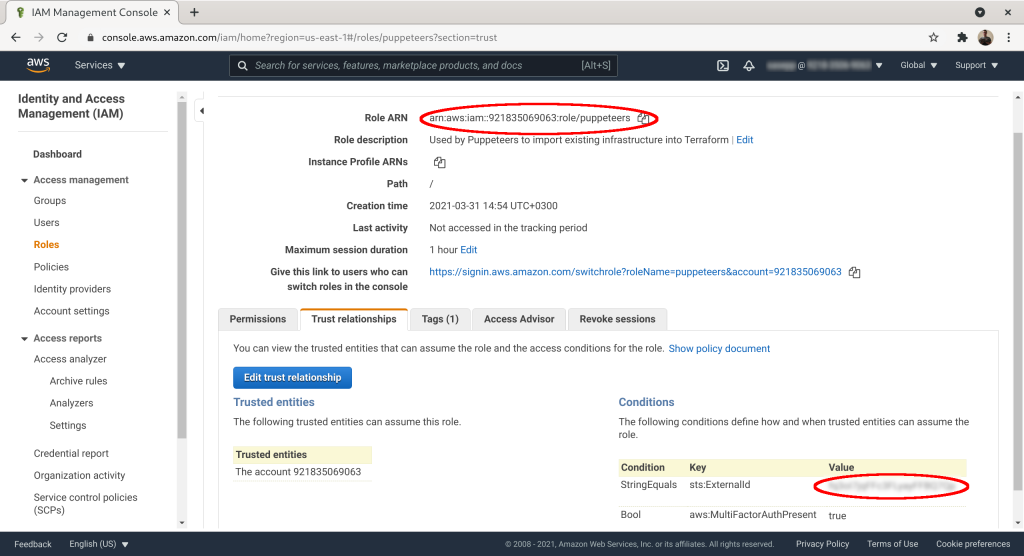
The last and final step is to send std:ExternalID and RoleARN to Puppeteers using the contact form. Then Puppeteers' employees can assume the role you created for them, provided they have two-factor authentication turned on in their AWS account.


